In this KB, we will publish a service on Paloalto firewall on the cloud.
First, let’s prepare the environment.
1- Create required networks and subnets:
For our example with Palo Alto firewall, we need one network for management access, a network for internal, and another one for external.
There are two ways to create resources in Openstack, a graphical user interface by using the Horizon dashboard, and the other way is by using CLI access.
To get API access, please follow the KB API access.
a- Creating Needed Networks:
Create the network using command:
openstack network create <NET_NAME>
b- Creating Corresponding Subnets:
Create a relative subnet using command:
openstack subnet create <SUBNET_NAME> --network <NET_NAME> --subnet-range <X.X.X.X/X>
Using the graphical user interface to create the needed networks and subnets.
Go to Network => Networking => Click on Create Network
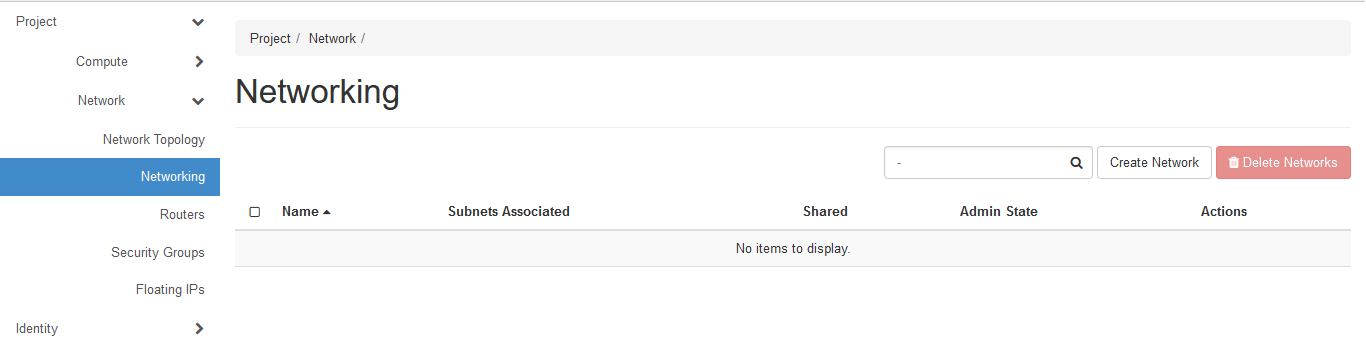
Give a network name
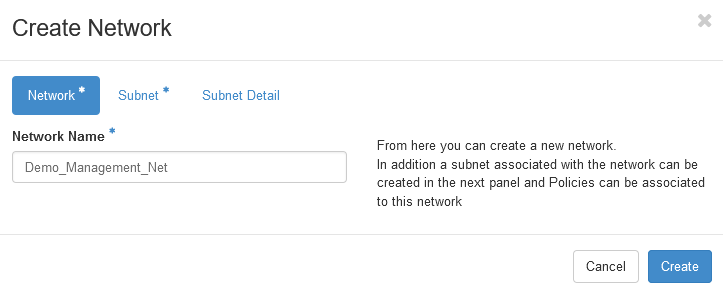
Give the subnet name and network address
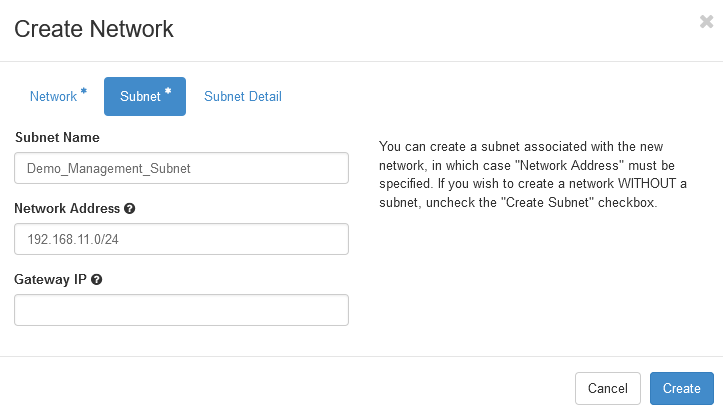
Then click create.
Repeat the above for any needed networks and subnets.
2- Creating Openstack Router:
Create a virtual router:
openstack router create <ROUTER_NAME>
Add router to needed subnet:
openstack router add subnet <ROUTER_NAME_OR_ID> <SUBNET_NAME_OR_ID>
Link the router to the external provider network:
openstack router set <ROUTER_NAME> --external-gateway <EXTERNAL_NETWORK_ID>
Note that, external network ID for RUH2 is
c975f064-d2b8-413c-9493-981f68bf887a, and for JED1 is80e37cda-1762-4d98-8e55-df3e33710295
You can also use the Horizon dashboard to create the needed router.
Go to Network => Routers => Click on Create Router
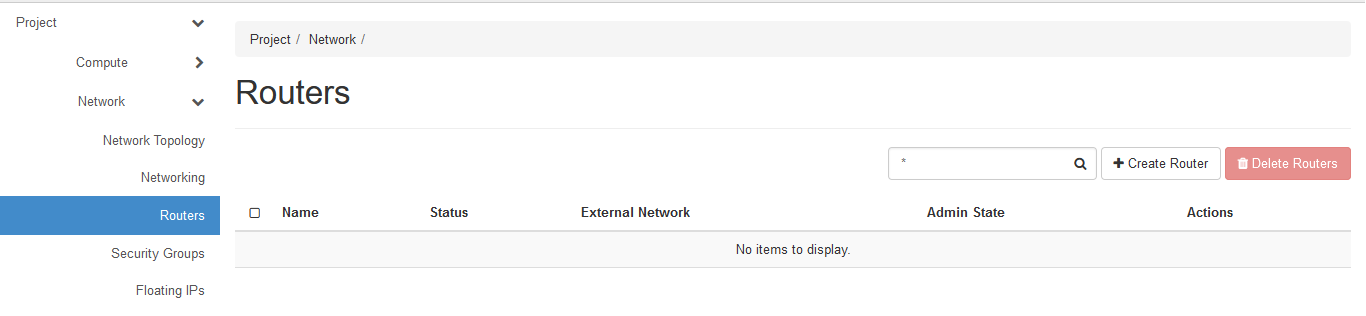
Give the Router name and click Create.
Now, after creating the router, you will need to set the router as an external one, to do that just click Set Gateway, then select the External Network
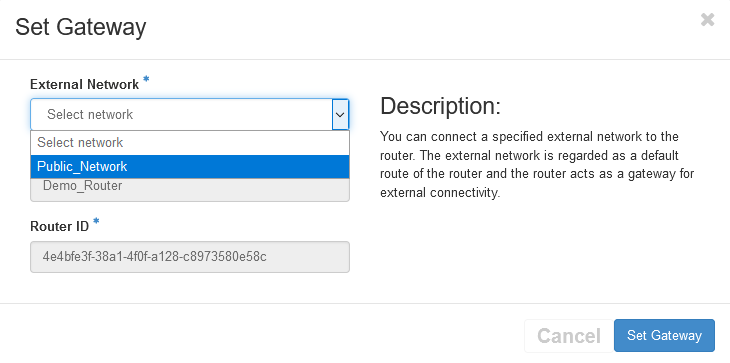
Again click Set Gateway
The next step is to add an interface to the created router from any needed subnet.
Click on the router name.
Click on Add Interface
Select the Subnet, and optionally you can select the IP Address.
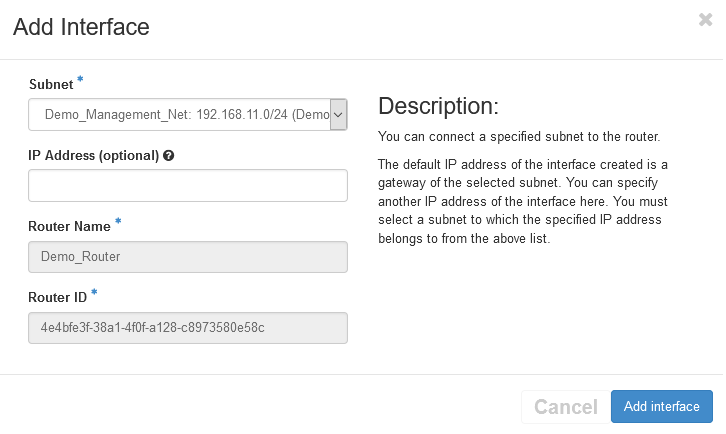
Then click Add Interface
Repeat adding interfaces as much as needed (You will need to add an interface for the external subnet as well)
3- Creating Security Groups:
The next step is to create a security group. You can create a security group from GUI or from CLI.
a- From CLI:
openstack security group create <SEC_GROUP_NAME> --description "Security Group for Paloalto Firewall"
Add needed rules:
openstack security group rule create <SEC_GROUP_NAME> \
--protocol tcp --dst-port 443:443 --remote-ip 0.0.0.0/0
b- From GUI:
Got to Network => Security Groups => Click Create Security Group
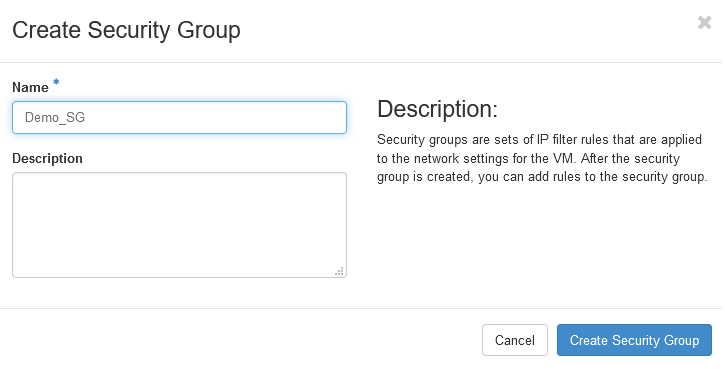 Give the security group name and click
Give the security group name and click Create Security Group
Click Manage Rules
Click Add Rule
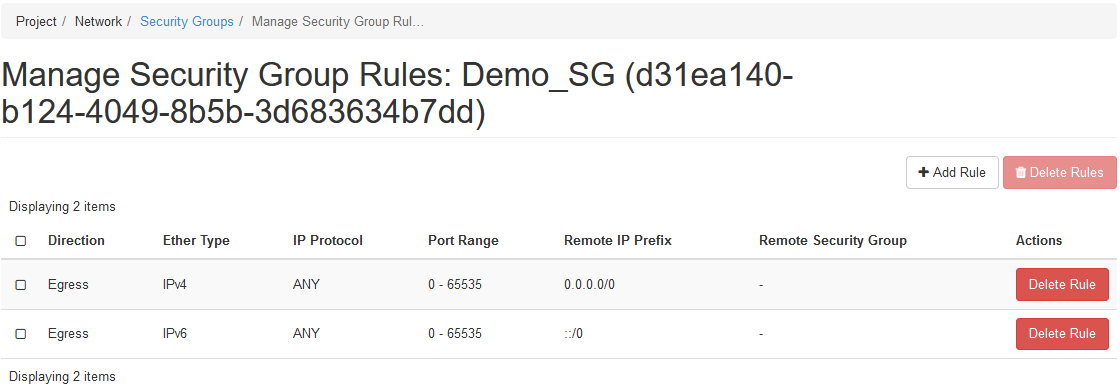
Add select HTTPS
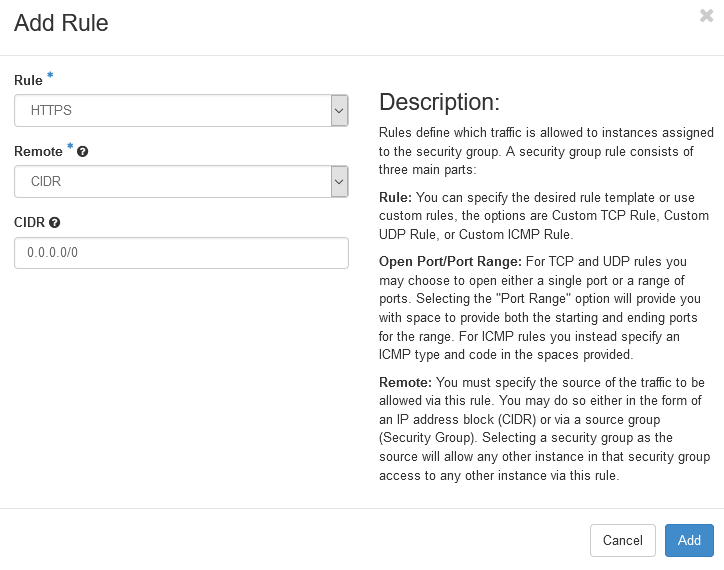
Add any additional needed rules
4- Creating Paloalto Instance:
Now, we will create the Paloalto FW instance.
a- From CLI:
Use the following command to create the instance:
openstack server create \
--flavor <FLAVOR_NAME> --image <IMAGE_ID> --availability-zone <ZONE_NAME> --security-group default --security-group <SEC_GROUP_NAME> \
--network <MANAGEMENT_NET_ID> --network <NET1_ID> --network <NET2_ID> --network <NET3_ID> --network <NET4_ID> \
--boot-from-volume <VOLUME_SIZE> --max 1 \
--wait <FW_NAME>
In this demo we simplify the code and used
--networkflag, for more advanced use cases, refer to the ‘–nic’ parameter. Palo Alto required more than 300G for the volume size.
In case of FW high available mode, please use a different zone for the other node.
b- Create the FW instance from GUI:
Please follow this KB virtual-server
Then assign the a floating IPs to the instance by using the following KB Allocate a Floating IP
In case you will add a FIP for the management interface, you will need to add another FIP for the dataplane external interface.
Based on your choice, you can use the same external FIP for multiple services or one for each service. To use different FIPs on the same interface in HA mode, please use this KB VIP
Second, Configure Paloalto Firewall
Now you have a running Paloalto FW, to access the FW use the URL https://MANAGEMENT_IP
Click Advanced then Accept the Risk and Continue
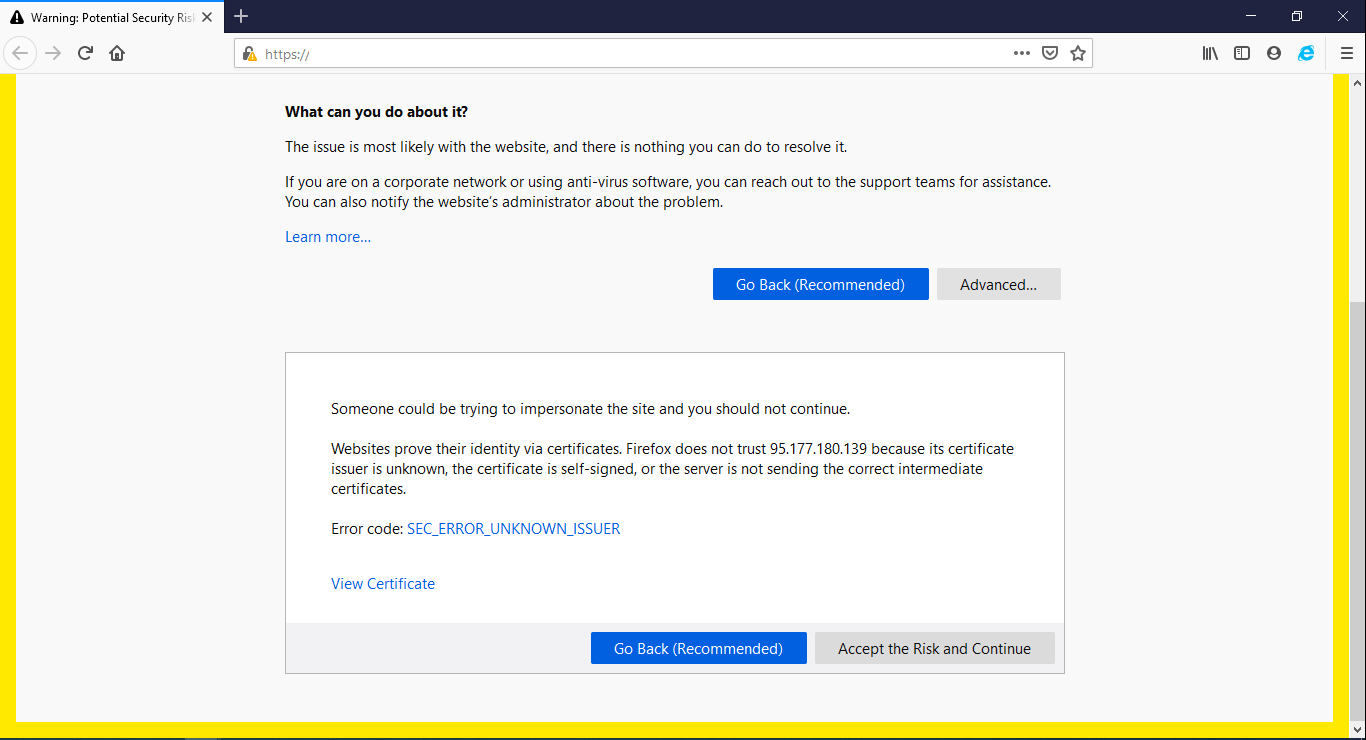
Enter the default credentials.

Configure the Network settings:
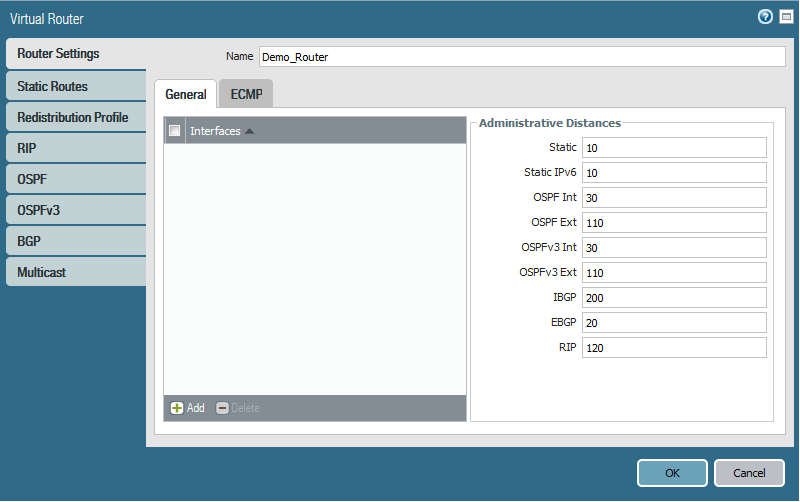
a- Create and configure a new virtual router:
Go to Network => Virtual Router => Add
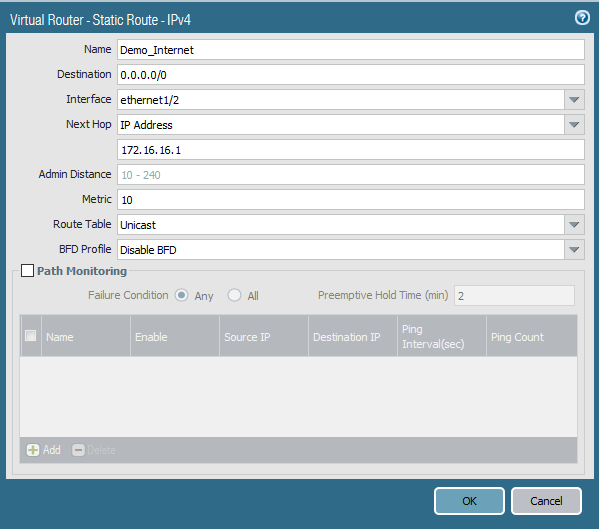
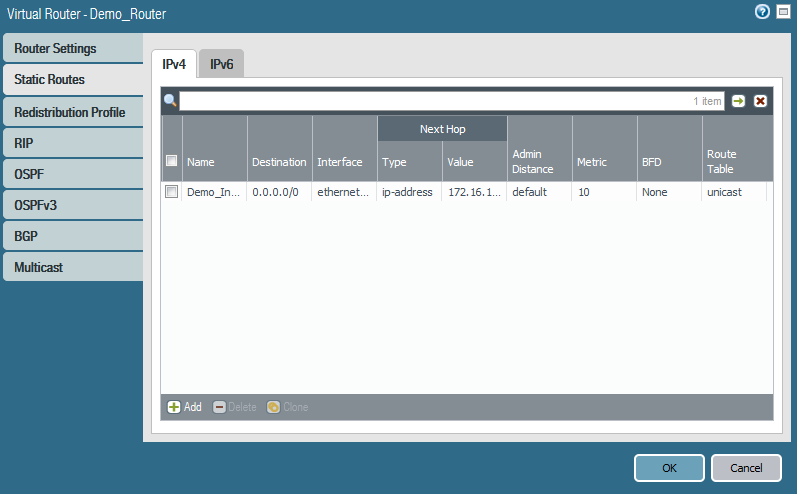
 Add static route through the external interface
Add static route through the external interface
b- Create required Zones:
Go to Network => Zones => Add
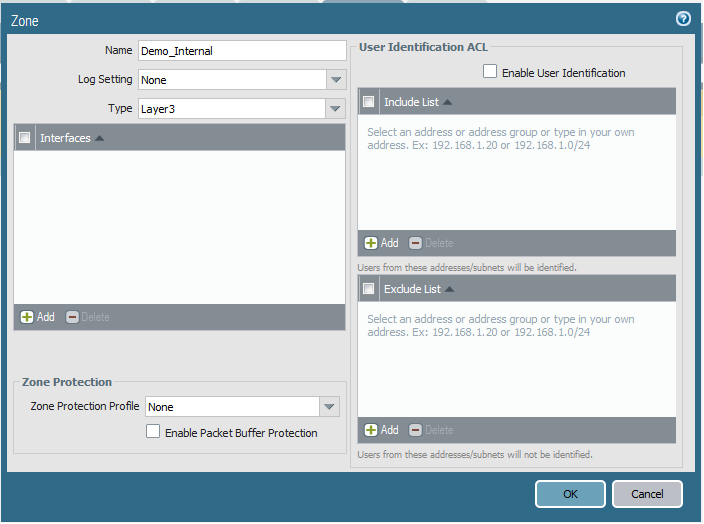
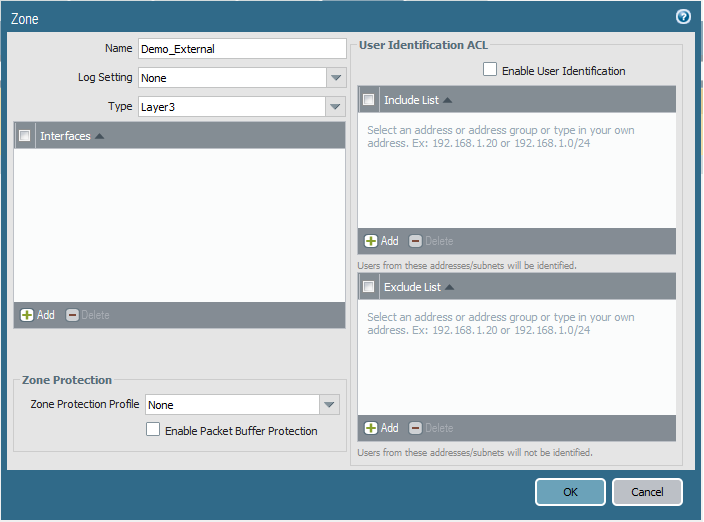
c- Configure Network Interfaces:
Go to Network => Interfaces
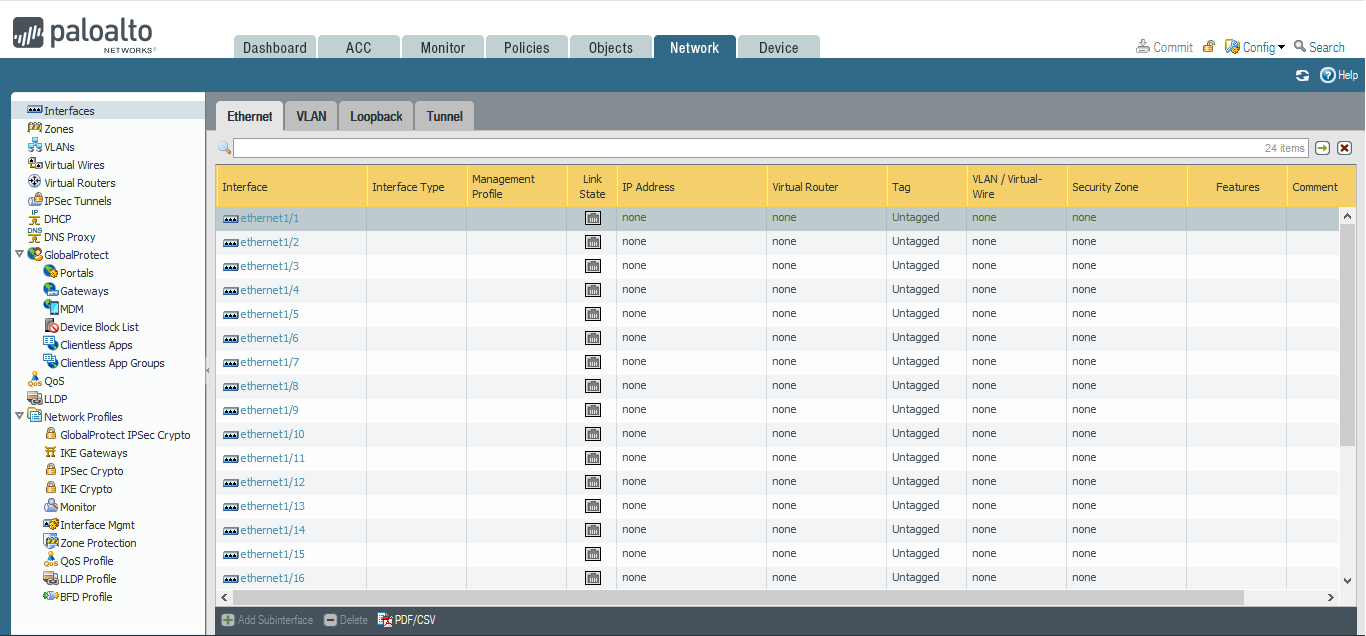
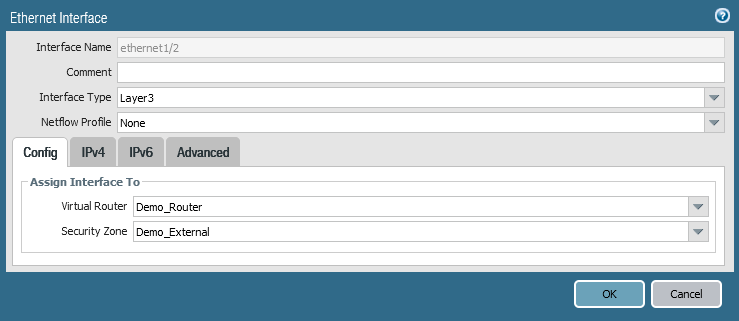
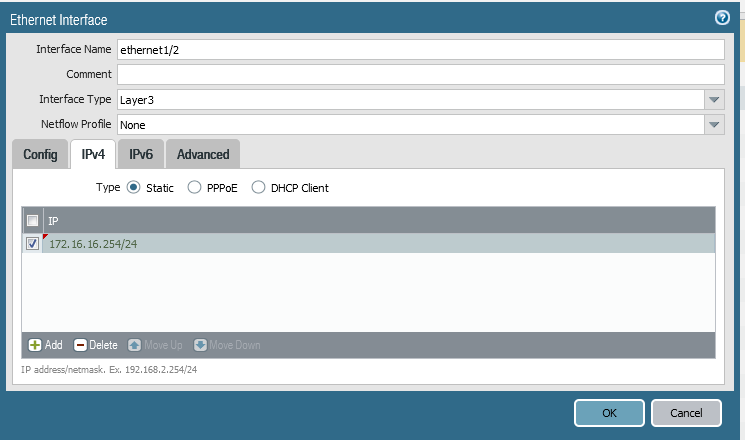
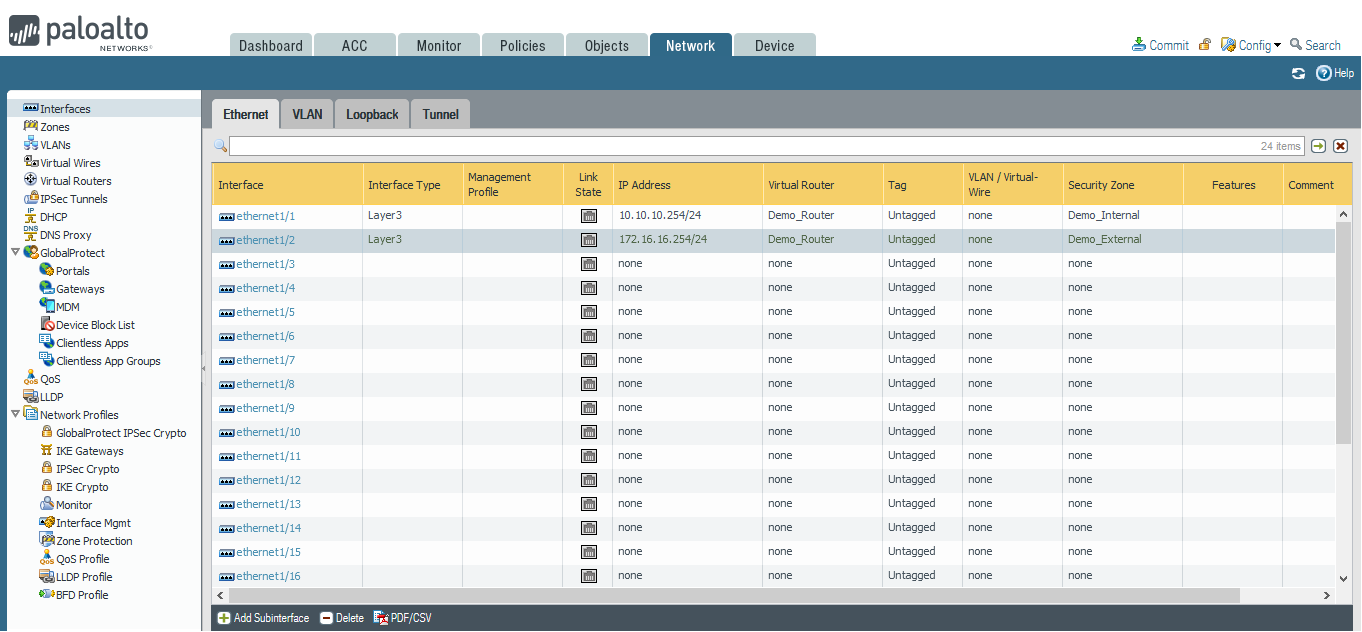
Repeat for all interfaces
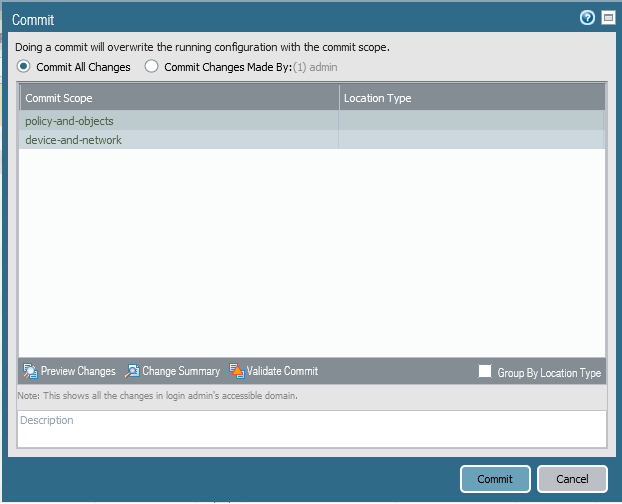
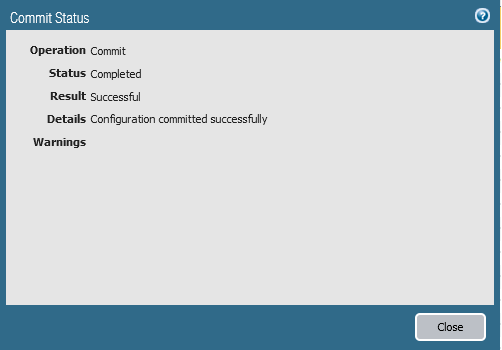
Click Commit
d- Add needed Objects:
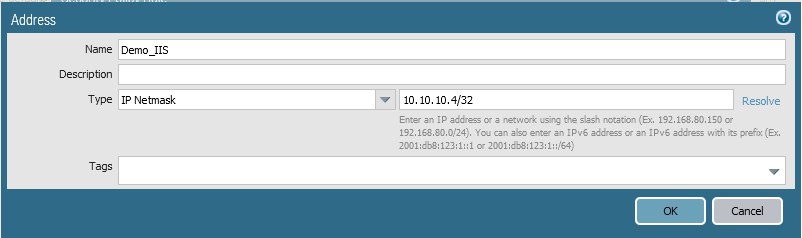
For each service, you will need two objects, first is the external VIP corresponding to the FIP, and the other is the internal IP of the server that is running the service.
Add internal server
Go to Objects => Addresses => click Add
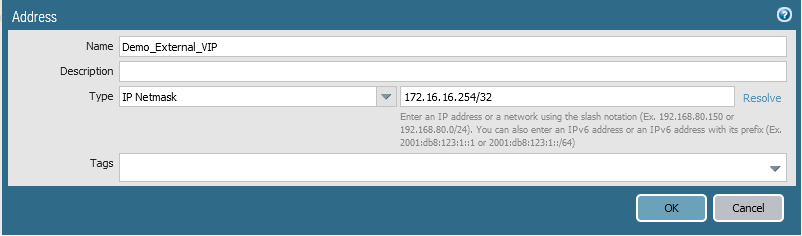
Add external VIP that is assigned to the Floating IP
e- Add Nat Policy:
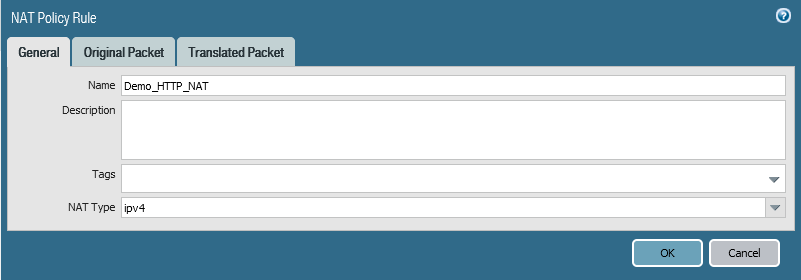
Go to Policies => NAT => Click Add.
Give the policy the Name.
We will do a source NAT and make sure to enable Bi-directional as follow:
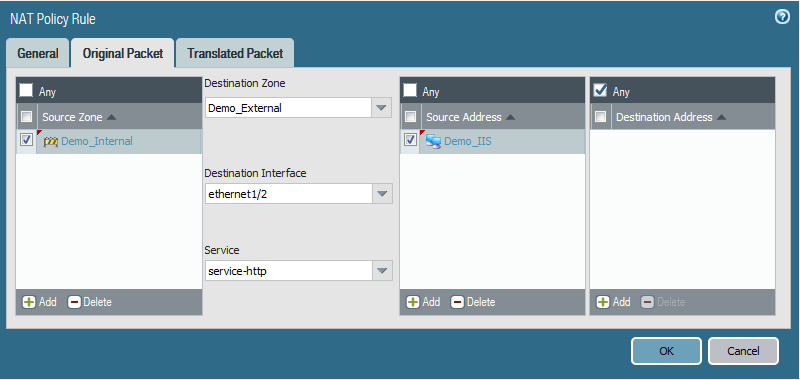
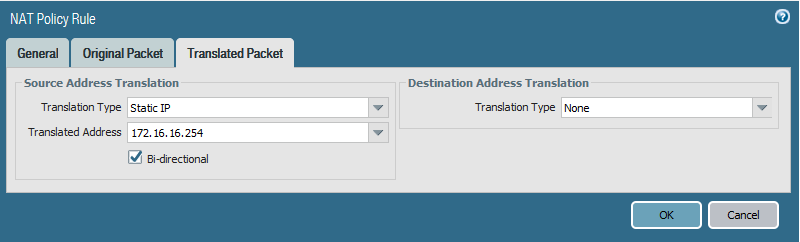
The translated address will be the VIP that is assigned with the FIP
f- Create needed Security Polices:
In this case our service is HTTP service, So first we must allow HTTP port on the Openstack security group.
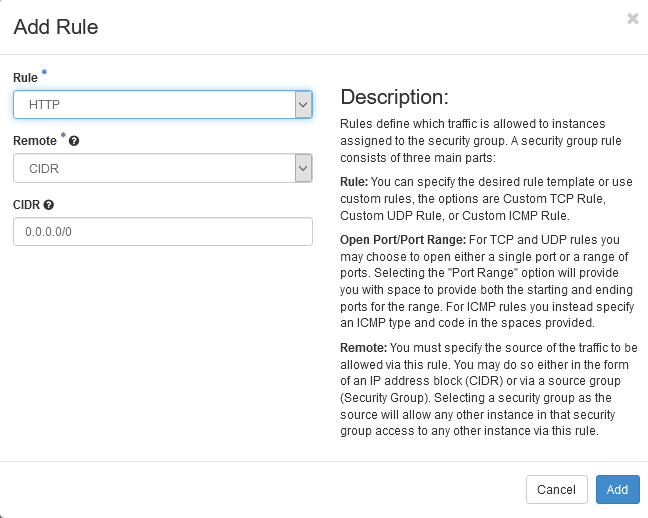 Then Create the needed FW Security Policies.
Then Create the needed FW Security Policies.
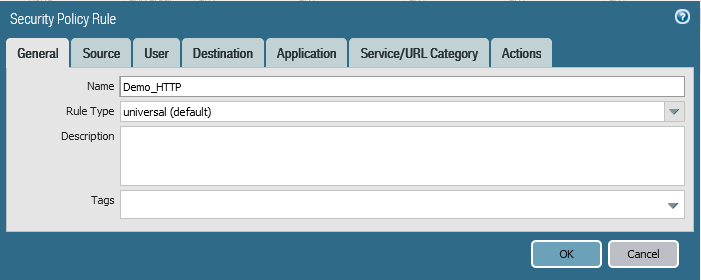
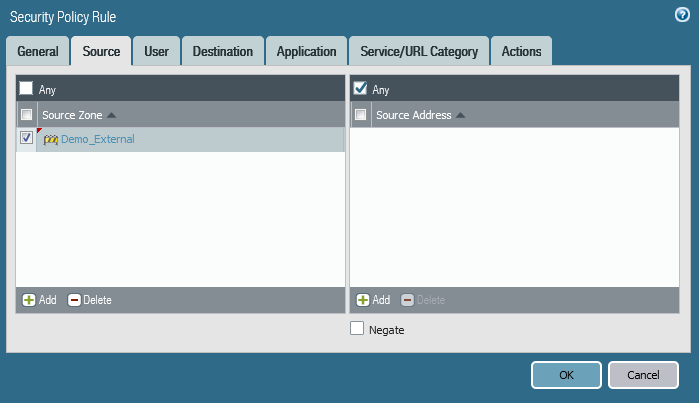
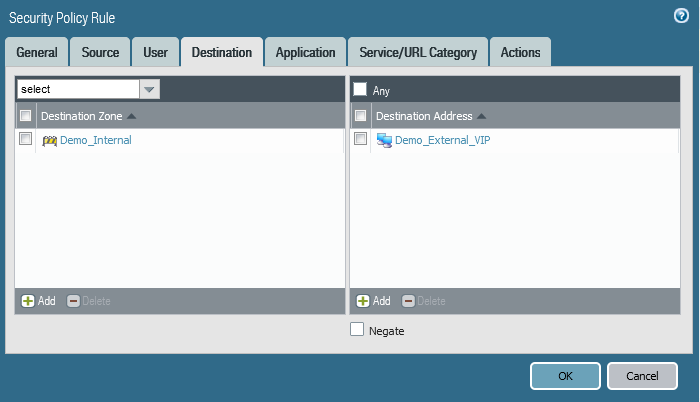
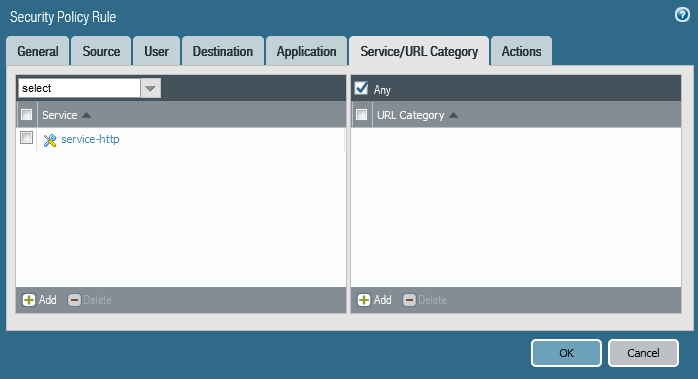
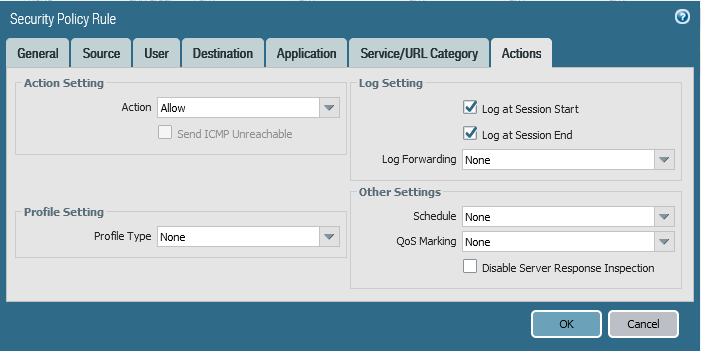
Finally, Click Commit
Now your service is published and accessible from outside.
To publish more than one service, you will need to assign more than one FIP (If needed) to the external interface, and use the associate VIP during the configuration of Paloalto Firewall.